The printing nightmare is eternal.
What you need to know
- Print Spooler vulnerabilities remain at large.
- CISA has had to address the topic.
- After all the effort to stop the threats, there's still an exploitation method in the wild.
Windows Print Spooler, PrintNightmare, and all the associated printer headaches comprise the story that just won't go away. It all started when researchers exposed an exploit, thinking it'd already been patched by Microsoft (spoiler: It hadn't been). Microsoft then released an emergency patch to deal with it, though that patch was easily undermined and had the unintended side effect of causing some printers to not work.
Then, as the mess grew ever messier, the Cybersecurity and Infrastructure Security Agency (CISA) sent out warnings and guidance to all Federal Civilian Executive Branch agencies, signaling that the issue was serious enough to warrant U.S. government attention. And now, there's a new Windows Print Spooler vulnerability making the rounds, formally designated as CVE-2021-34481 (via BleepingComputer).
Here's Microsoft's executive summary of CVE-2021-34481:
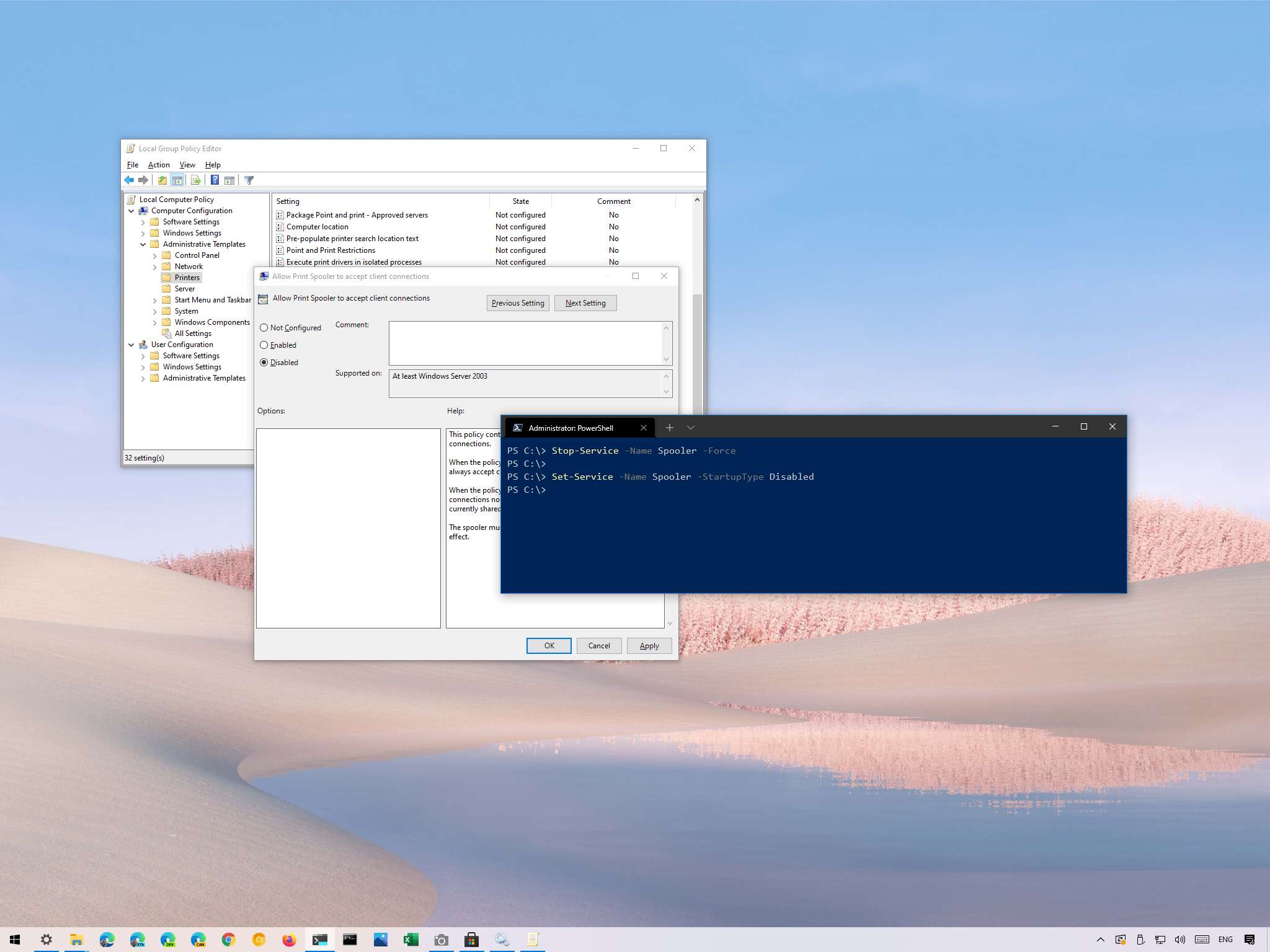
An elevation of privilege vulnerability exists when the Windows Print Spooler service improperly performs privileged file operations. An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. An attacker must have the ability to execute code on a victim system to exploit this vulnerability. The workaround for this vulnerability is stopping and disabling the Print Spooler service.
Dragos security researcher Jacob Baines told BleepingComputer that because this is a local vulnerability, it's not directly related to PrintNightmare. With that said, it's certainly related to the trail of headaches left by PrintNightmare for Windows Print Spooler and serves as the cherry on top of a vulnerability-riddled sundae.





0 comments:
Post a Comment